Hi Briolet,
daar zit hem nou juist net het probleem.
Omdat ik het
draadje hebt gevolgd kan ik nu geen export maken vanuit de VPNpackage
Ik ben nu tegen een aantal dingen aangelopen. Misschien dat iemand mij kan helpen...
- Via een iOS device werkt alles prima. Ik heb de certificaten aangemaakt en via iTunes alle bestanden netjes ingeladen. Geen problemen. Het werkt, en ik krijg netjes te zien in de VPNserver dat er 1 huidige verbinding is en met welk account.
- Het 2e punt is dat ik de losse bestanden, CA.crt, client.crt en client.key. (of CA.crt, gebruikersnaam.crt en gebruikersnaam.key) en ta.key niet kan inladen in Tunnelblick. Dit wordt niet geaccepteerd. Ik kan alleen het bestand openvpn.ovpn in Tunnelblick krijgen.
Nu zit juist daar het probleem.
Als ik dit bestand direct inlaad krijg ik de volgende foutmelding.
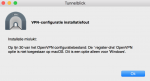
De regel "register-dns" heb ik verwijderd en krijg dan de volgende melding
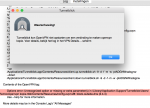
Dus ook deze "Block-outside-dns" verwijderd. - Poging 3 was aan de beurt. Maar voordat ik daaraan begon dacht ik.... Ik moet een Inline certifcate maken. Zo gezegd, zo gedaan.
Zie hier:
[i]# Dit config bestand dient nog aangepast worden aan jouw situatie
# Wijzig alleen wat gevraagd wordt!
remote DDNS 1194 ### Extern IP adres of DDNS-naam of Domein-naam. Meerdere regels zijn mogelijk
#cert aaaaaa.crt ### Heb je voor meerdere gebruikers certificaten/keys gemaakt dan "gebruikersnaam.crt"
#key bbbbbb.key ### Heb je voor meerdere gebruikers certificaten/keys gemaakt dan "gebruikersnaam.key"
# Onderstaande "dhcp-option DNS" hoeft niet gebruikt te worden,
# dan wordt de standaard DNS instelling van de client gebruikt.
# Wil je dat wel dan moet het een geldig DNS server IP zijn
# Hetzij een eigen DNS server (b.v. op de Diskstation)
# Of publieke DNS server (b.v. 8.8.8.8 van Google)
# Wanneer je het wel gebruikt moet het # weggehaalt worden
# Er kunnen er meerdere opgegeven worden
dhcp-option DNS 8.8.8.8 ### IP van DNS server 1
#dhcp-option DNS vul.hier.ip2.in ### IP van DNS server 2
# Wat hier onder staat hoeft niet gewijzigd te worden
################################################################
#ca CA.crt ###
verb 4
redirect-gateway def1
dev tun
proto udp
pull
tls-client
remote-cert-tls server
cipher AES-256-CBC
prng SHA256 32
auth SHA256
tls-version-min 1.2 or-highest
#tls-auth ta.key 1 ###
fast-io
comp-lzo
reneg-sec 0
auth-user-pass
auth-nocache
<ca>
-----BEGIN CERTIFICATE-----
MIIFujCCA6KgAwIBAgIBATANBgkqhkiG9w0BAQsFADB1MQswCQYDVQQGEwI/PzEL
MAkGA1UECBMCPz8xCzAJBgNVBAcTAj8/MQ0wCwYDVQQKEwRPVlBOMREwDwYDVQQL
EwhTZWN1cml0eTELMAkGA1UEAxMCQ0ExHTAbBgkqhkiG9w0BCQEW.........
-----END CERTIFICATE-----
</ca>
<cert>
-----BEGIN CERTIFICATE-----
MIIFvTCCA6WgAwIBAgIBAzANBgkqhkiG9w0BAQsFADB1MQswCQYDVQQGEwI/PzEL
MAkGA1UECBMCPz8xCzAJBgNVBAcTAj8/MQ0wCwYDVQQKEwRPVlBOMREwDwYDVQQL
EwhTZWN1cml0eTELMAkGA1UEAxMCQ0ExHTAbBgkqhkiG9w0BCQEW............
-----END CERTIFICATE-----
</cert>
<key>
-----BEGIN RSA PRIVATE KEY-----
MIIJKAIBAAKCAgEArI7iVAqsU80jXRkA/VXZOCLfQEAZ6wMv5HCfMEQCPX92eU1p
NHl/6Ic5DqVtkHtcryPjQTV6SoitRrRxWLA910ge3HbZwxm9Pat8GdKfe14I2yuP
yWzU7RdE38U3OcvBxb4wcL2TIzyzb+hg2nLcbnV52iAcv/hViqfGkgXr......
-----END RSA PRIVATE KEY-----
</key>
<tls-auth>
-----BEGIN OpenVPN Static key V1-----
d662b6b9502d639096b3218b6c267586
b8316e273ee170e5e40a778ba6186938
60b4c5c1a06b902b81ed8494edddb27a
fd8318b882e4374ac1ca6c506......
-----END OpenVPN Static key V1-----
</tls-auth>
key-direction 1[/i]
En jahoor, ik krijg netjes verbinding.
Ik bekijk eerst mijn
IP adres voor het starten en als ik verbinding heb. Na het starten, via een andere omgeving dan thuis, zie ik netjes mijn WAN adres van Ziggo...
Zie het log hieronder:
[i]*Tunnelblick: OS X 10.13.3; Tunnelblick 3.7.4b (build 4921)
2018-02-06 11:42:50 *Tunnelblick: Attempting connection with RemcoVPNphoneNW using shadow copy; Set nameserver = 769; monitoring connection
2018-02-06 11:42:50 *Tunnelblick: openvpnstart start RemcoVPNphoneNW.tblk 1337 769 0 1 0 1065264 -ptADGNWradsgnw 2.4.4-openssl-1.0.2n
2018-02-06 11:42:51 *Tunnelblick: openvpnstart log:
OpenVPN started successfully. Command used to start OpenVPN (one argument per displayed line):
/Applications/Tunnelblick.app/Contents/Resources/openvpn/openvpn-2.4.4-openssl-1.0.2n/openvpn
--daemon
--log
/Library/Application Support/Tunnelblick/Logs/-SUsers-SRemco-SLibrary-SApplication Support-STunnelblick-SConfigurations-SRemcoVPNphoneNW.tblk-SContents-SResources-Sconfig.ovpn.769_0_1_0_1065264.1337.openvpn.log
--cd
/Library/Application Support/Tunnelblick/Users/Remco/RemcoVPNphoneNW.tblk/Contents/Resources
--setenv
IV_GUI_VER
"net.tunnelblick.tunnelblick 4921 3.7.4b (build 4921)"
--verb
3
--config
/Library/Application Support/Tunnelblick/Users/Remco/RemcoVPNphoneNW.tblk/Contents/Resources/config.ovpn
--verb
3
--cd
/Library/Application Support/Tunnelblick/Users/Remco/RemcoVPNphoneNW.tblk/Contents/Resources
--management
127.0.0.1
1337
--management-query-passwords
--management-hold
--script-security
2
--up
/Applications/Tunnelblick.app/Contents/Resources/client.up.tunnelblick.sh -9 -d -f -m -w -ptADGNWradsgnw
--down
/Applications/Tunnelblick.app/Contents/Resources/client.down.tunnelblick.sh -9 -d -f -m -w -ptADGNWradsgnw
2018-02-06 11:42:50 *Tunnelblick: openvpnstart starting OpenVPN
2018-02-06 11:42:51 *Tunnelblick: Established communication with OpenVPN
2018-02-06 11:42:51 OpenVPN 2.4.4 x86_64-apple-darwin [SSL (OpenSSL)] [LZO] [LZ4] [PKCS11] [MH/RECVDA] [AEAD] built on Dec 7 2017
2018-02-06 11:42:51 library versions: OpenSSL 1.0.2n 7 Dec 2017, LZO 2.10
2018-02-06 11:42:51 MANAGEMENT: TCP Socket listening on [AF_INET]127.0.0.1:1337
2018-02-06 11:42:51 Need hold release from management interface, waiting...
2018-02-06 11:42:51 MANAGEMENT: Client connected from [AF_INET]127.0.0.1:1337
2018-02-06 11:42:51 MANAGEMENT: CMD 'pid'
2018-02-06 11:42:51 MANAGEMENT: CMD 'state on'
2018-02-06 11:42:51 MANAGEMENT: CMD 'state'
2018-02-06 11:42:51 MANAGEMENT: CMD 'bytecount 1'
2018-02-06 11:42:51 MANAGEMENT: CMD 'hold release'
2018-02-06 11:43:08 MANAGEMENT: CMD 'username "Auth" "RemcoVPNphone"'
2018-02-06 11:43:08 MANAGEMENT: CMD 'password [...]'
2018-02-06 11:43:08 NOTE: the current --script-security setting may allow this configuration to call user-defined scripts
2018-02-06 11:43:08 Outgoing Control Channel Authentication: Using 256 bit message hash 'SHA256' for HMAC authentication
2018-02-06 11:43:08 Incoming Control Channel Authentication: Using 256 bit message hash 'SHA256' for HMAC authentication
2018-02-06 11:43:08 MANAGEMENT: >STATE:1517913788,RESOLVE,,,,,,
2018-02-06 11:43:08 TCP/UDP: Preserving recently used remote address: [AF_INET][b]WAN IP[/b]:1194
2018-02-06 11:43:08 Socket Buffers: R=[196724->196724] S=[9216->9216]
2018-02-06 11:43:08 UDP link local (bound): [AF_INET][undef]:1194
2018-02-06 11:43:08 UDP link remote: [AF_INET][b]WAN IP[/b]:1194
2018-02-06 11:43:08 MANAGEMENT: >STATE:1517913788,WAIT,,,,,,
2018-02-06 11:43:08 MANAGEMENT: >STATE:1517913788,AUTH,,,,,,
2018-02-06 11:43:08 TLS: Initial packet from [AF_INET][b]WAN IP[/b]:1194, sid=6dc75d0a fcda2ba5
2018-02-06 11:43:10 VERIFY OK: depth=1, C=??, ST=??, L=??, O=OVPN, OU=Security, CN=CA, emailAddress=rootca@vpn.vpn
2018-02-06 11:43:10 VERIFY KU OK
2018-02-06 11:43:10 Validating certificate extended key usage
2018-02-06 11:43:10 ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web Server Authentication
2018-02-06 11:43:10 VERIFY EKU OK
2018-02-06 11:43:10 VERIFY OK: depth=0, C=??, ST=??, L=??, O=OVPN, OU=Security, CN=Server, emailAddress=servercert@vpn.vpn
2018-02-06 11:43:12 Control Channel: TLSv1.2, cipher TLSv1/SSLv3 DHE-RSA-AES256-GCM-SHA384, 4096 bit RSA
2018-02-06 11:43:12 [Server] Peer Connection Initiated with [AF_INET][b]WAN IP[/b]:1194
2018-02-06 11:43:13 MANAGEMENT: >STATE:1517913793,GET_CONFIG,,,,,,
2018-02-06 11:43:13 SENT CONTROL [Server]: 'PUSH_REQUEST' (status=1)
2018-02-06 11:43:13 PUSH: Received control message: 'PUSH_REPLY,route 192.168.179.0 255.255.255.0,route 172.16.0.0 255.255.255.0,sndbuf 0,rcvbuf 0,route-gateway 172.16.0.1,topology subnet,ping 10,ping-restart 60,ifconfig 172.16.0.2 255.255.255.0'
2018-02-06 11:43:13 OPTIONS IMPORT: timers and/or timeouts modified
2018-02-06 11:43:13 OPTIONS IMPORT: --sndbuf/--rcvbuf options modified
2018-02-06 11:43:13 Socket Buffers: R=[196724->196724] S=[9216->9216]
2018-02-06 11:43:13 OPTIONS IMPORT: --ifconfig/up options modified
2018-02-06 11:43:13 OPTIONS IMPORT: route options modified
2018-02-06 11:43:13 OPTIONS IMPORT: route-related options modified
2018-02-06 11:43:13 Outgoing Data Channel: Cipher 'AES-256-CBC' initialized with 256 bit key
2018-02-06 11:43:13 Outgoing Data Channel: Using 256 bit message hash 'SHA256' for HMAC authentication
2018-02-06 11:43:13 Incoming Data Channel: Cipher 'AES-256-CBC' initialized with 256 bit key
2018-02-06 11:43:13 Incoming Data Channel: Using 256 bit message hash 'SHA256' for HMAC authentication
2018-02-06 11:43:13 Opening utun (connect(AF_SYS_CONTROL)): Resource busy (errno=16)
2018-02-06 11:43:13 Opening utun (connect(AF_SYS_CONTROL)): Resource busy (errno=16)
2018-02-06 11:43:13 Opened utun device utun2
2018-02-06 11:43:13 do_ifconfig, tt->did_ifconfig_ipv6_setup=0
2018-02-06 11:43:13 MANAGEMENT: >STATE:1517913793,ASSIGN_IP,,172.16.0.2,,,,
2018-02-06 11:43:13 /sbin/ifconfig utun2 delete
ifconfig: ioctl (SIOCDIFADDR): Can't assign requested address
2018-02-06 11:43:13 NOTE: Tried to delete pre-existing tun/tap instance -- No Problem if failure
2018-02-06 11:43:13 /sbin/ifconfig utun2 172.16.0.2 172.16.0.2 netmask 255.255.255.0 mtu 1500 up
2018-02-06 11:43:13 /sbin/route add -net 172.16.0.0 172.16.0.2 255.255.255.0
add net 172.16.0.0: gateway 172.16.0.2
2018-02-06 11:43:13 /Applications/Tunnelblick.app/Contents/Resources/client.up.tunnelblick.sh -9 -d -f -m -w -ptADGNWradsgnw utun2 1500 1570 172.16.0.2 255.255.255.0 init
**********************************************
Start of output from client.up.tunnelblick.sh
Disabled IPv6 for 'Thunderbolt Ethernet'
Disabled IPv6 for 'Wi-Fi'
Disabled IPv6 for 'iPhone USB'
Disabled IPv6 for 'Bluetooth PAN'
Disabled IPv6 for 'Thunderbolt Bridge'
Disabled IPv6 for 'VPN Thuis'
Retrieved from OpenVPN: name server(s) [ 8.8.8.8 ], search domain(s) [ ] and SMB server(s) [ ] and using default domain name [ openvpn ]
Not aggregating ServerAddresses because running on OS X 10.6 or higher
Setting search domains to 'openvpn' because running under OS X 10.6 or higher and the search domains were not set manually (or are allowed to be changed) and 'Prepend domain name to search domains' was not selected
Saved the DNS and SMB configurations so they can be restored
Changed DNS ServerAddresses setting from '89.101.251.228 89.101.251.229' to '8.8.8.8'
Changed DNS SearchDomains setting from '' to 'openvpn'
Changed DNS DomainName setting from 'home' to 'openvpn'
Did not change SMB NetBIOSName setting of ''
Did not change SMB Workgroup setting of ''
Did not change SMB WINSAddresses setting of ''
DNS servers '8.8.8.8' will be used for DNS queries when the VPN is active
The DNS servers include only free public DNS servers known to Tunnelblick.
Flushed the DNS cache via dscacheutil
/usr/sbin/discoveryutil not present. Not flushing the DNS cache via discoveryutil
Notified mDNSResponder that the DNS cache was flushed
Setting up to monitor system configuration with process-network-changes
End of output from client.up.tunnelblick.sh
**********************************************
2018-02-06 11:43:17 *Tunnelblick: No 'connected.sh' script to execute
2018-02-06 11:43:17 /sbin/route add -net [b]WAN IP[/b] 192.168.179.1 255.255.255.255
add net [b]WAN IP[/b]: gateway 192.168.179.1
2018-02-06 11:43:17 /sbin/route add -net 0.0.0.0 172.16.0.1 128.0.0.0
add net 0.0.0.0: gateway 172.16.0.1
2018-02-06 11:43:17 /sbin/route add -net 128.0.0.0 172.16.0.1 128.0.0.0
add net 128.0.0.0: gateway 172.16.0.1
2018-02-06 11:43:17 MANAGEMENT: >STATE:1517913797,ADD_ROUTES,,,,,,
2018-02-06 11:43:17 /sbin/route add -net 192.168.179.0 172.16.0.1 255.255.255.0
route: writing to routing socket: File exists
add net 192.168.179.0: gateway 172.16.0.1: File exists
2018-02-06 11:43:17 /sbin/route add -net 172.16.0.0 172.16.0.1 255.255.255.0
route: writing to routing socket: File exists
add net 172.16.0.0: gateway 172.16.0.1: File exists
2018-02-06 11:43:17 Initialization Sequence Completed
2018-02-06 11:43:17 MANAGEMENT: >STATE:1517913797,CONNECTED,SUCCESS,172.16.0.2,[b]WAN IP[/b],1194,,
2018-02-06 11:43:22 *Tunnelblick process-network-changes: A system configuration change was ignored
2018-02-06 11:43:22 *Tunnelblick: This computer's apparent public IP address changed from 31.161.157.192 before connection to [b]WAN IP[/b] after connection[/i]
Echter blijf ik nu met het volgende probleem zitten en dat is dat de verbinding die ik met dit certificaat maak niet wordt gezien in de VPNserver

Ik dan dus wel gewoon internetten, maar ik vraag me dus af of het wel allemaal goed gaat?
Wie kan mij helpen en misschien kijken wat ik fout gedaan heb of een oplossing bedanken?
Dank.
Remco[/list]






 Vergelijkbare onderwerpen (3)
Vergelijkbare onderwerpen (3)